Android Pentesting Course Overview
This intensive Android course goes far beyond automated scanning and basic MobSF walkthroughs. Instead, it teaches you how attackers actually break Android applications - from reverse engineering APKs and bypassing root detection to exploiting insecure data storage, WebView vulnerabilities, IPC flaws, exported components, deep link abuse, API weaknesses, and SSL pinning bypass.
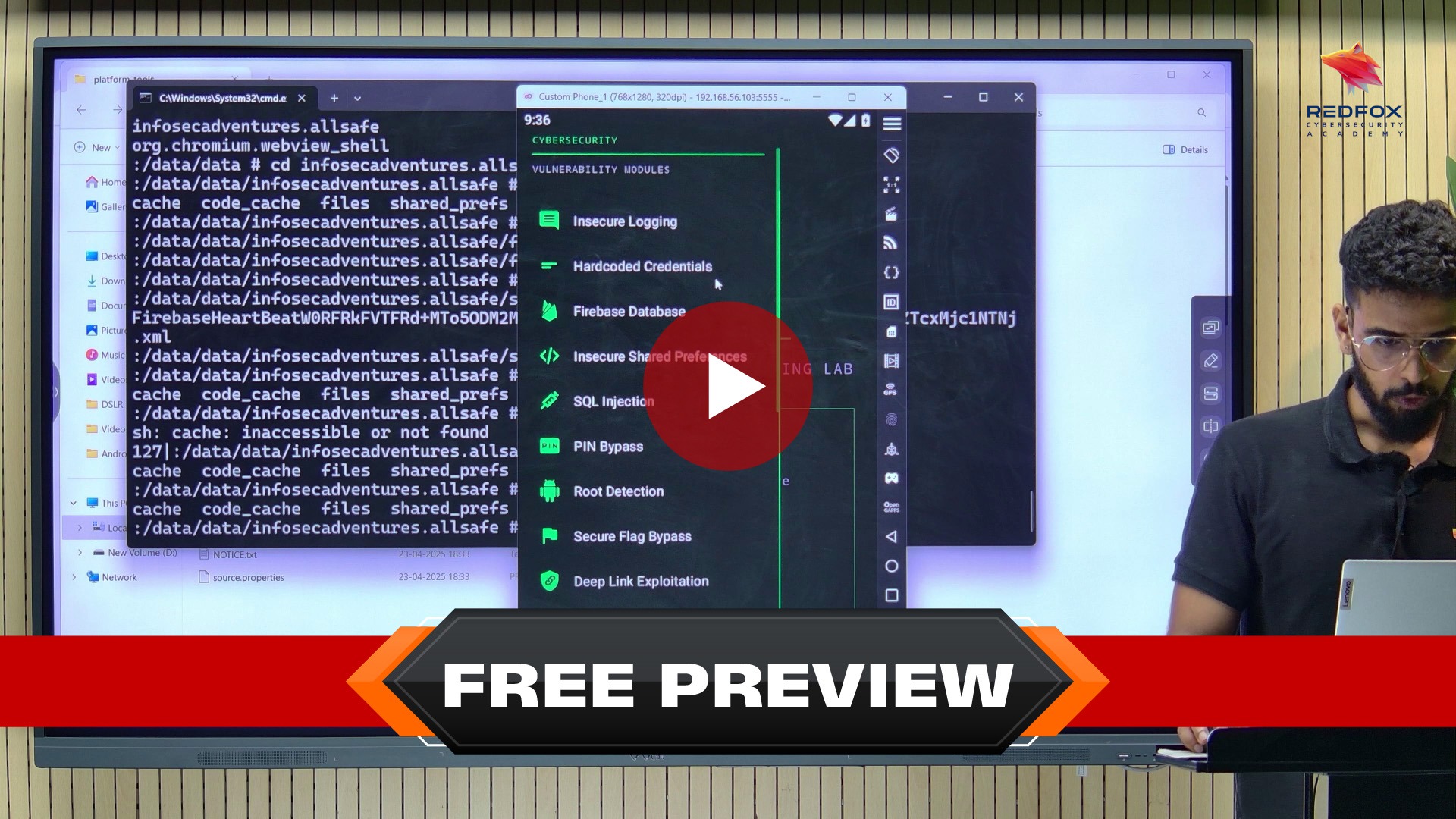
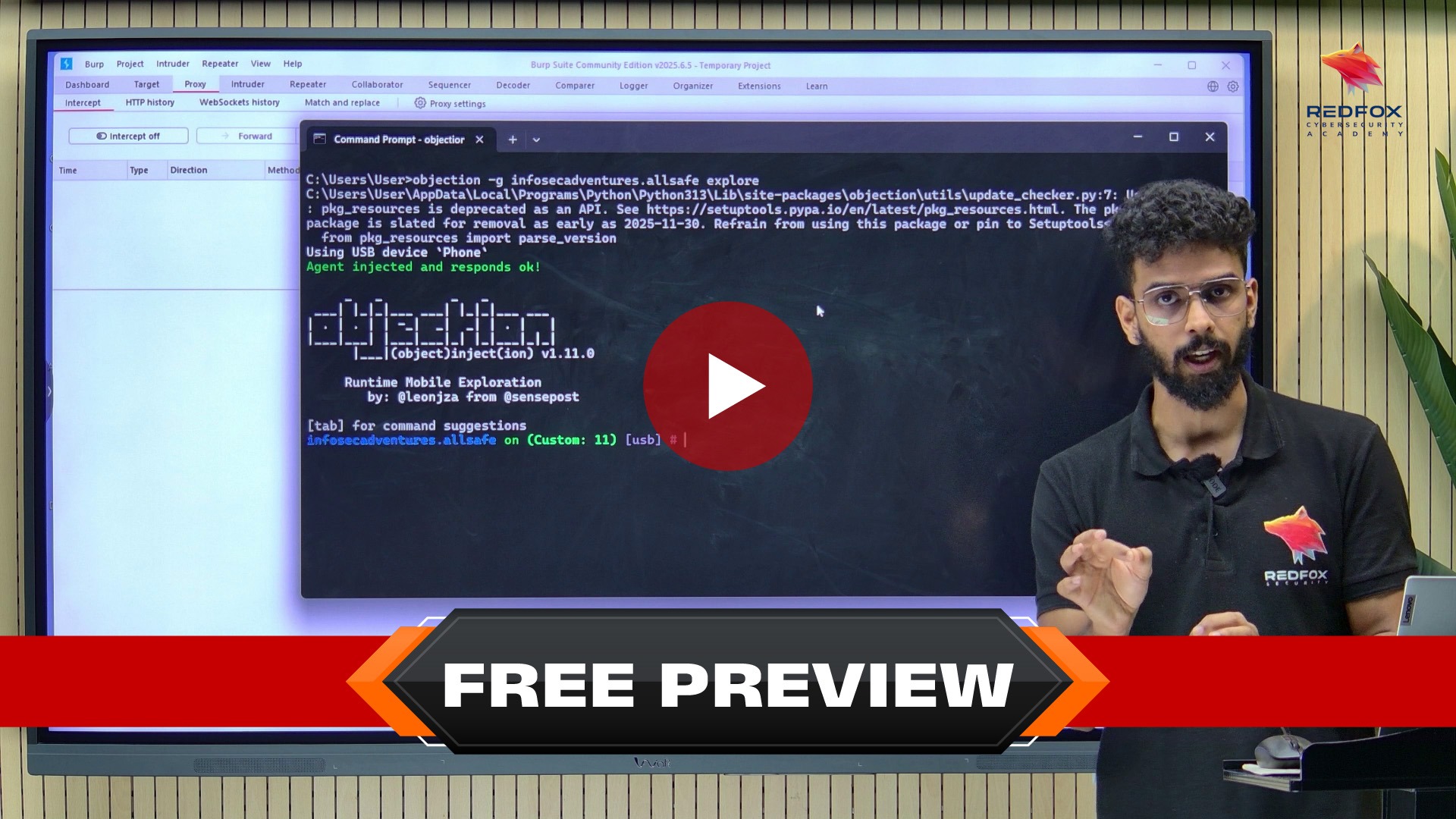
Using real-world Android applications and industry-standard tools like Frida, Objection, Burp Suite, MobSF, JADX, Ghidra, ADB, and APKTool, participants perform live exploitation exercises that replicate actual mobile penetration testing engagements. This is not passive slide-based training - it is practical, lab-driven Android pentesting that covers the complete attack surface of modern Android apps from APK extraction to runtime hook injection.
By the end of the program, you’ll earn the Certified Android Application Penetration Tester (CAAPT) - a practical certification that validates your Android exploitation skills through hands-on assessment, not multiple-choice theory. Whether you're expanding from web to mobile pentesting, targeting Android bug bounties, or strengthening your red team capabilities, this course gives you the real-world edge needed in modern mobile pentesting.
Why Android Pentesting is a High-Value Skill?
- Most pentesters avoid mobile
- Android apps expose tokens, APIs, business logic
- Hackers who want to learn how to assess the security of Android apps and devices.
- Mobile findings pay higher bounties
- Enterprises struggle to test mobile apps properly
After This Course, You Will Be Able To
- Test production Android apps
- Bypass root & SSL pinning protections
- Extract sensitive data from APKs
- Write professional mobile pentest reports
- Confidently say “Yes” to Android pentest projects
Is Android Pentesting Course For You?
- You know basic pentesting or web security
-
You want to test real Android apps
- You want mobile pentesting or bug bounty skills
-
You’re tired of CTF-only knowledge
- You have foundational security or penetration testing knowledge and want to specialise in android penetration testing
-
You want rare, in-demand skills in mobile penetration testing
- You want Android app development
- You expect copy-paste exploits
- You’ve never used Burp or proxies before
- You prefer theory-heavy lectures instead of hands-on android pentesting labs
- You are only interested in defensive blue-team mobile security
- You want automated scanner results without understanding exploitation techniques
Who Should Take Android Pentesting Course Course?
- Individuals looking to break into the field of mobile security testing.
- Those interested in expanding their skills to Android app security and mobile pentesting.
- Hackers who want to learn how to assess the security of Android apps and devices.
- Individuals researching mobile vulnerabilities and exploitation techniques in Android environments.
- Developers interested in understanding Android security issues to secure their own apps.
Android Pentesting Course Curriculum
Android Pentesting Course
45 Learning Materials
Module 1: Course Introduction & Environment Setup
Course agenda
Android Pentesting Overview
OWASP Top 10
Android Architecture with Examples
Setting Up Android Pentesting Environment
Module 2: Static Analysis & Hardcoded Secrets
Static Analysis
Analyzing the Manifest File
Hardcoded Secrets
Manual Static Analysis (Practical)
MobSF
Module 3: Reporting Basics
Reporting
Module 4: Dynamic Analysis
Dynamic Analysis Overview
Module 5: Insecure Data Storage and Firebase Database
Insecure Data Storage
Insecure Data Storage Practical
Insecure Data Storage Reporting
Firebase Database
Firebase Database Practical
Module 6: Logging & Forensics
Insecure Logging
Insecure Logging Practical
Module 7: Drozer - Android Exploitation Framework
Drozer
Installation of the Drozer Tool
Drozer Practical
Module 8: Frida - Runtime Instrumentation
Frida Root Detection Bypass
Frida & its Use Cases
Configuring Frida & Objection on Desktop
Setting up Frida Server
Additional Resource
Module 9: SSL Pinning & Network Interception
SSL Certificate Pinning
Bypassing SSL Pinning
SSL Pinning Bypass Using Objection
SSL Pinning Bypass Using Frida
Module 10: StrandHogg & Android Components (Theory)
StrandHogg Vulnerability
Understanding Android Components
Module 11: StrandHogg Practical & Mitigations
StrandHogg Practical
References and Blogs
Mitigation Strategies
Module 12: WebView Security
Insecure WebView Implementation (Theory)
Insecure WebView Implementation (Practical)
Module 13: Real-World Pentest Case Study
Real-World Pentest Scenario
Module 14: Advanced Reporting
Reporting
Module 15: Course Wrap-Up
Course Summary & Exam Guidance
Module 16: Course Resources
Android Pentesting Course PPT
Drozer Cheat Sheet
Mobile Reporting Template
Strandhogg Files
Android Pentesting Course Instructor

Tarak Sakhardande
Senior Security Consultant
Tarak Sakhardande is a cybersecurity expert with deep expertise in web app security, mobile testing, and Active Directory pentesting. He specializes in finding vulnerabilities and improving digital defenses.
Certified Android Application Penetration Tester (CAAPT)
After completing the course, you’ll take a hands-on certification exam that tests your skills in a real-world scenario.
Submit your professional report, pass the exam, and earn your CAAPT – Certified Android Application Penetration Tester certificate. Use the certificate to boost your resume, share it on LinkedIn, and stand out in cybersecurity job interviews.

Key Takeaways
- Understand Android architecture, permissions, and how Android apps are packaged and deployed.
- Master the tools and techniques for static and dynamic analysis of Android apps.
- Learn how to root Android devices and bypass root detection mechanisms.
- Identify and exploit vulnerabilities in Android apps, including those from the OWASP Mobile Top 10.
- Gain hands-on experience with real-world vulnerable apps, including practical challenges like weak cryptography, insecure data storage, and improper input validation.
- Apply practical knowledge in real-world scenarios.
System Requirements
- Operating System: Windows, Linux, or macOS with virtualization support enabled.
- Memory: A minimum of 8 GB RAM.
- Storage: At least 256 GB of free disk space.
If you only know web pentesting, you are replaceable.
Mobile makes you rare.
Ready to Master the Art of Pentesting?
Affordable Price
Unlock your potential with affordable upskilling! Our unbeatable course prices are your chance to level up without breaking the bank.
Lifetime Access
Acquire lifetime access to our resources when you buy our courses. Gain knowledge today and unlock a lifetime of learning.
Certificate of Completion
Upon completing our course, you'll receive a certificate of completion to showcase your new skills. Add it to your resume or LinkedIn profile.
Hands-On Experience
Get hands-on experience with real-world scenarios and challenges, giving you practical skills that you can apply immediately in your career.
Expert Instructors
Learn from industry experts with years of experience in pentesting, who are passionate about sharing their knowledge and helping you succeed.
Flexible Learning
Whether you're a beginner or an experienced professional, our courses are designed to meet you where you are and help you reach your goals.
Get in Touch
Have a question, need assistance, or want to collaborate? We’re here to help!
Whether you're looking for cutting-edge cybersecurity solutions or expert training or want to learn more about our services, contact us today.
By clicking on Continue, I accept the Terms & Conditions,
Privacy Policy