Testimonials
HP
January 7
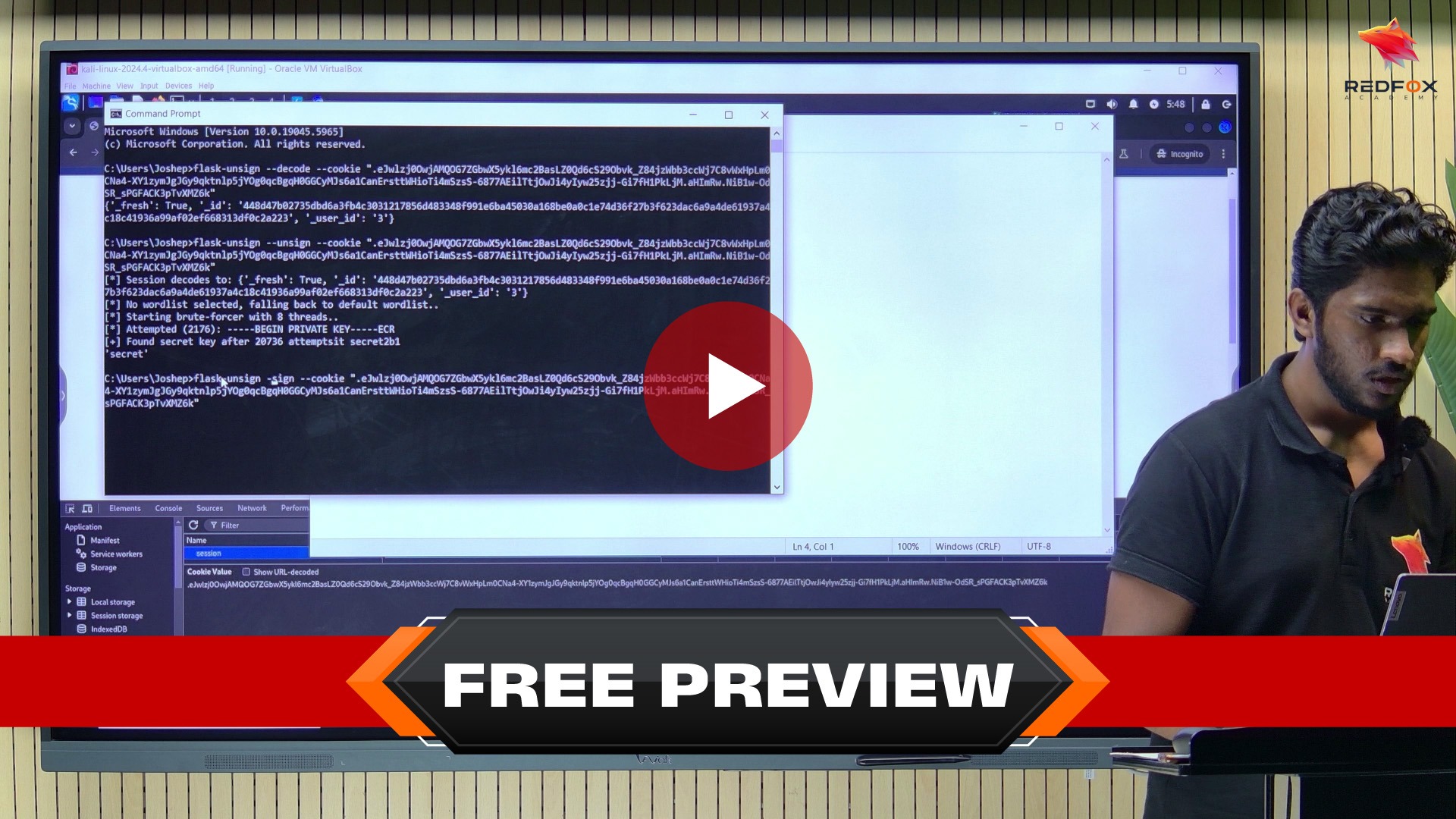
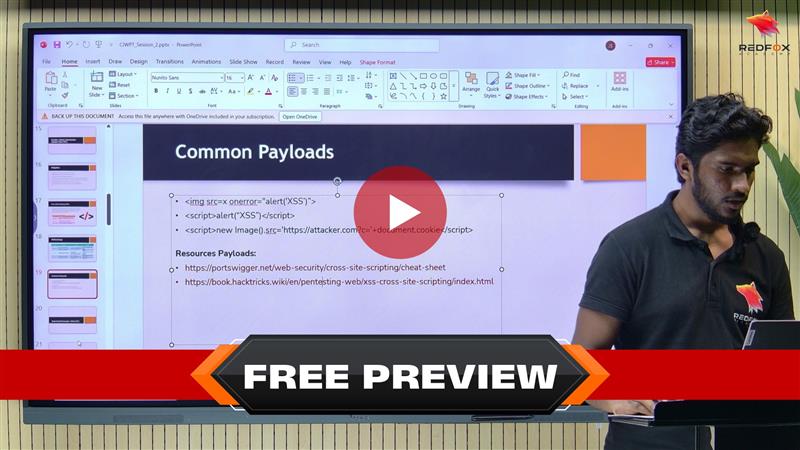
Before this course, I knew a bit about web security but had no idea how to practically apply it. This course changed that completely. Around 70% of the content is hands-on labs, which helped me learn by doing, not just listening. The instructor, Joseph Simon, explained things clearly and drew from his own cybersecurity experience. I now feel confident identifying and exploiting real web vulnerabilities.
Read more
Zoe Martinez
October 27, 2025
I took this Web Hacking Basics Course to strengthen my security foundation, and it delivered. The labs made up most of the learning and were very realistic. Joseph Simon shared real-world insights from his professional experience that simply don’t come from slides. By the end, I could practically apply what I learned instead of just understanding theory.
Read more
PA
December 1, 2025
This course was exactly what I needed to kickstart my journey in web security. Around 70% of the course involved hands-on labs and practical exercises, which accelerated my learning. Joseph Simon’s approach of showing how attackers think made complex concepts easy to grasp. I now feel significantly more prepared to tackle web security challenges.
Read more
Elina Georgiou
October 28, 2025
The practical nature of this course is what impressed me most. Most of the time was spent in labs, actually testing and exploiting vulnerabilities. Joseph Simon’s professional background in cybersecurity made every session feel grounded in reality. I genuinely feel that I can apply what I learned in real work environments now.
Read more
Samuel Njoroge
October 16, 2025
If you want to learn web hacking by actually doing it, this course is perfect. Roughly 70% of the content is hands-on, and it made all the difference for me. Joseph Simon explained everything in a simple, practical way and gave real-life examples from his own experience. I now have confidence in finding and fixing web vulnerabilities.
Read more
Maria Rossi
September 23, 2025
I appreciated how this course focused on practical learning. The labs were challenging but extremely helpful, and most of the course was spent putting concepts into practice. Joseph Simon didn’t just teach theory, he shared how things work in real engagements based on his professional experience. I can already see improvements in how I approach web security tasks.
Read more