Testimonials
AN
January 6
The Windows Red Teaming Course by Redfox Cybersecurity Academy completely changed how I approach Active Directory security. The hands-on labs covering Kerberoasting, DCSync attacks, and Golden Ticket creation were highly practical and realistic. Performing lateral movement and privilege escalation in live environments built real confidence. This course significantly accelerated my professional growth.
Read more
SN
This course is deeply technical and fully hands-on. Practicing NTLM relay attacks, BloodHound enumeration, and credential dumping in structured lab scenarios helped me truly understand adversary tradecraft. The focus on chaining attacks across Windows domains was extremely valuable. After completing the course, I felt far more prepared for advanced red team engagements.
Read more
DB
January 7
What stands out in the Windows Red Teaming Course by Redfox Cybersecurity Academy is the realism of the labs. From domain enumeration to DCShadow and advanced persistence mechanisms, everything is executed practically. Learning how to abuse Kerberos and maintain stealth inside a domain environment gave me a strong technical edge. The skills I gained directly contributed to my career advancement.
Read more
RK
October 27, 2025
The practical learning approach in this course is unmatched. I spent most of the time performing DCSync attacks, SPN exploitation, process injection, and Defender evasion techniques. Instead of just learning tools, I learned methodology. This course gave me the confidence to handle complex internal assessments and strengthened my professional profile.
Read more
Michael Carter
December 1, 2025
The Windows Red Teaming Course by Redfox Cybersecurity Academy provides serious depth into Active Directory exploitation. The structured modules on lateral movement, privilege escalation, and post-exploitation persistence were reinforced with hands-on lab exercises. Completing this program helped me transition into more advanced and challenging security roles.
Read more
TS
October 28, 2025
From Kerberoasting chains to NTLM relay exploitation and BloodHound path analysis, every module in this course is practical and execution-focused. The lab-driven format ensures that concepts are not just understood but applied. This training significantly enhanced my technical expertise and gave me a clear advantage in my career progression.
Read more
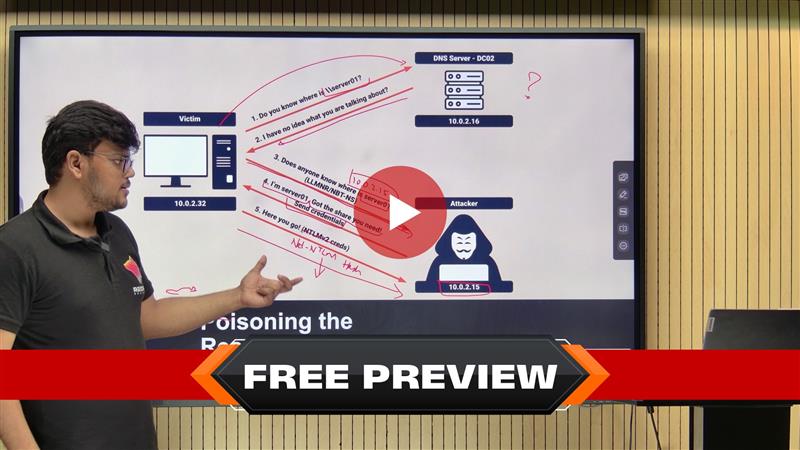
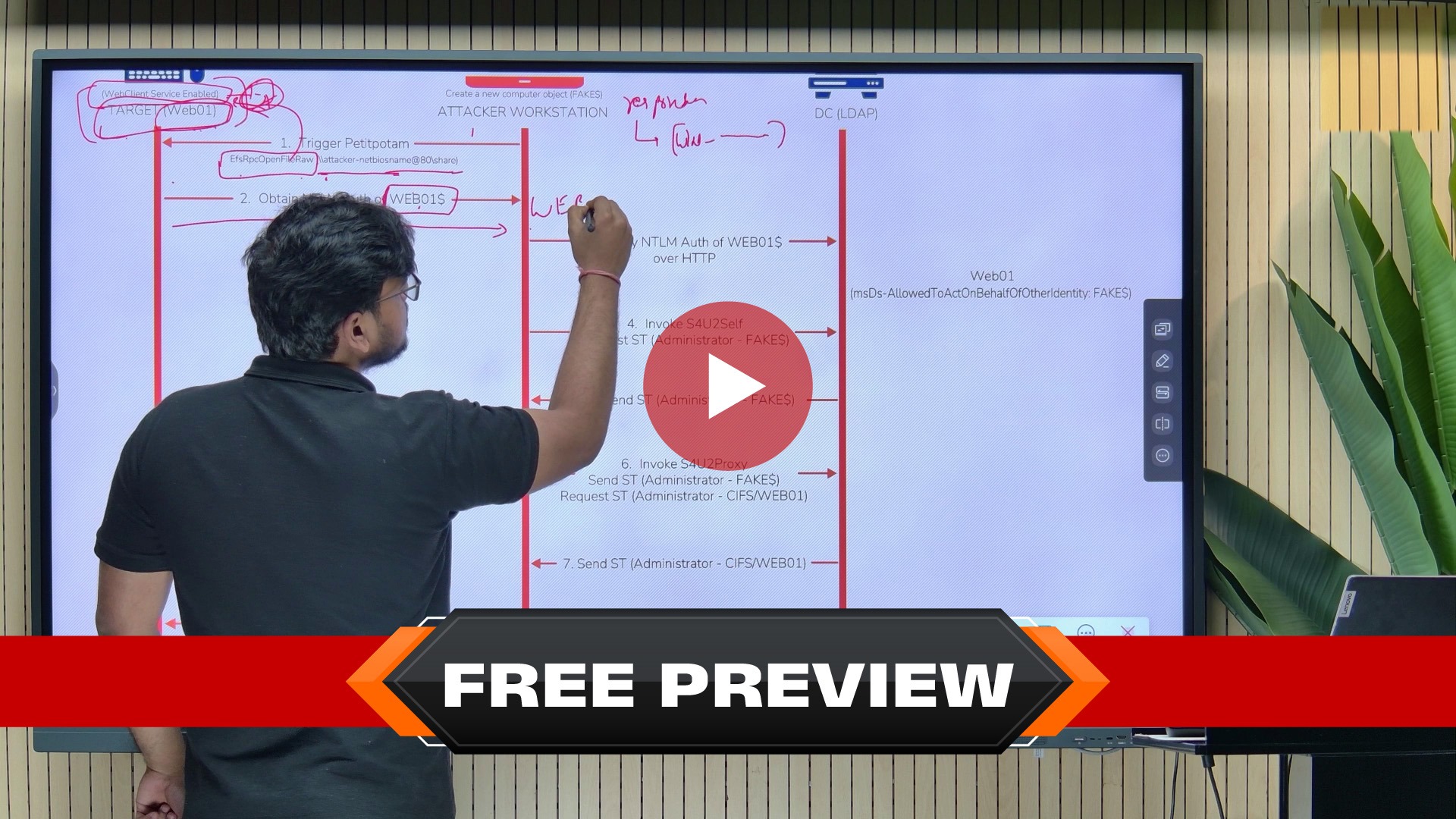
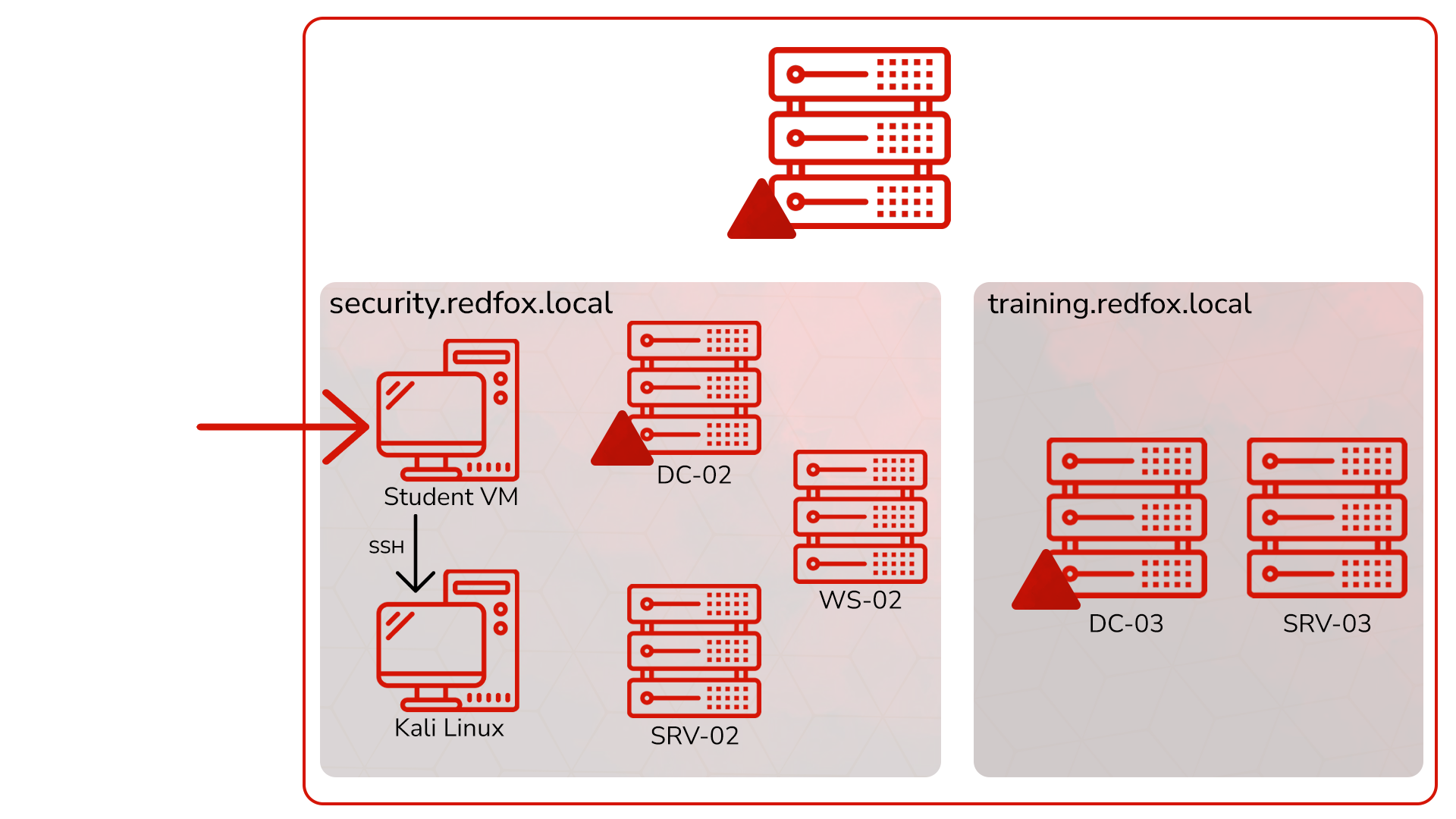

.jpg)