iOS Pentesting Course
If you want to break real iOS apps like a professional - this is non-negotiable.
iOS Pentesting Course Overview
- A detailed introduction to iOS architecture, security features, and common vulnerabilities in iOS applications.
- Step-by-step guidance on setting up an iOS pentesting environment, including tools like Xcode and jailbreaking techniques.
- Hands-on experience in static analysis, including reverse engineering iOS apps, analyzing binary files, and using tools like MobSF and Ghidra.
- Dynamic analysis techniques such as debugging, runtime manipulation, and network traffic interception using tools like Frida and Objection.
- Advanced exploitation techniques focusing on insecure data storage, API attacks, and bypassing app security mechanisms.
Why Most People Fail at iOS Pentesting?
- iOS internals feel opaque and undocumented
- Jailbreaking & Frida setups break constantly
- Swift + Obj-C confuse even experienced pentesters
- Most courses stop at MobSF screenshots
- No real apps, no real exploits
Is iOS Pentesting Course For You?
- You want to break real production iOS apps
- You already know basic security and want mobile specialization
-
You’re targeting pentest roles / bug bounties
-
You prefer terminals, scripts, and tools over slides
- You want a beginner iOS dev course
- You’re scared of jailbreaking devices
- You want copy-paste checklists
- You’re looking for theory-only content
Key Takeaways
- Learn the fundamentals of iOS architecture, security features, and distribution models.
- Perform effective reconnaissance and information gathering
- Hands-on experience with tools like Xcode, Frida, Ghidra, and MobSF.
- Ability to identify and exploit vulnerabilities in iOS apps, including insecure data storage and API flaws.
- Master runtime manipulation, network traffic analysis, and bypassing app security mechanisms.
- Apply practical knowledge in real world scenarios
iOS Pentesting Course Curriculum
iOS Pentesting Course
37 Learning Materials
Module 1: iOS Pentesting Course Overview
Course Overview
Module 2: iOS Basics and Setting up the Environment
Agenda
iOS Security Architecture
iOS Application Architecture
iOS Penetration Testing Methodology
Configuring Device
iOS Basics Recap
Module 3: Static Application Security Testing (SAST)
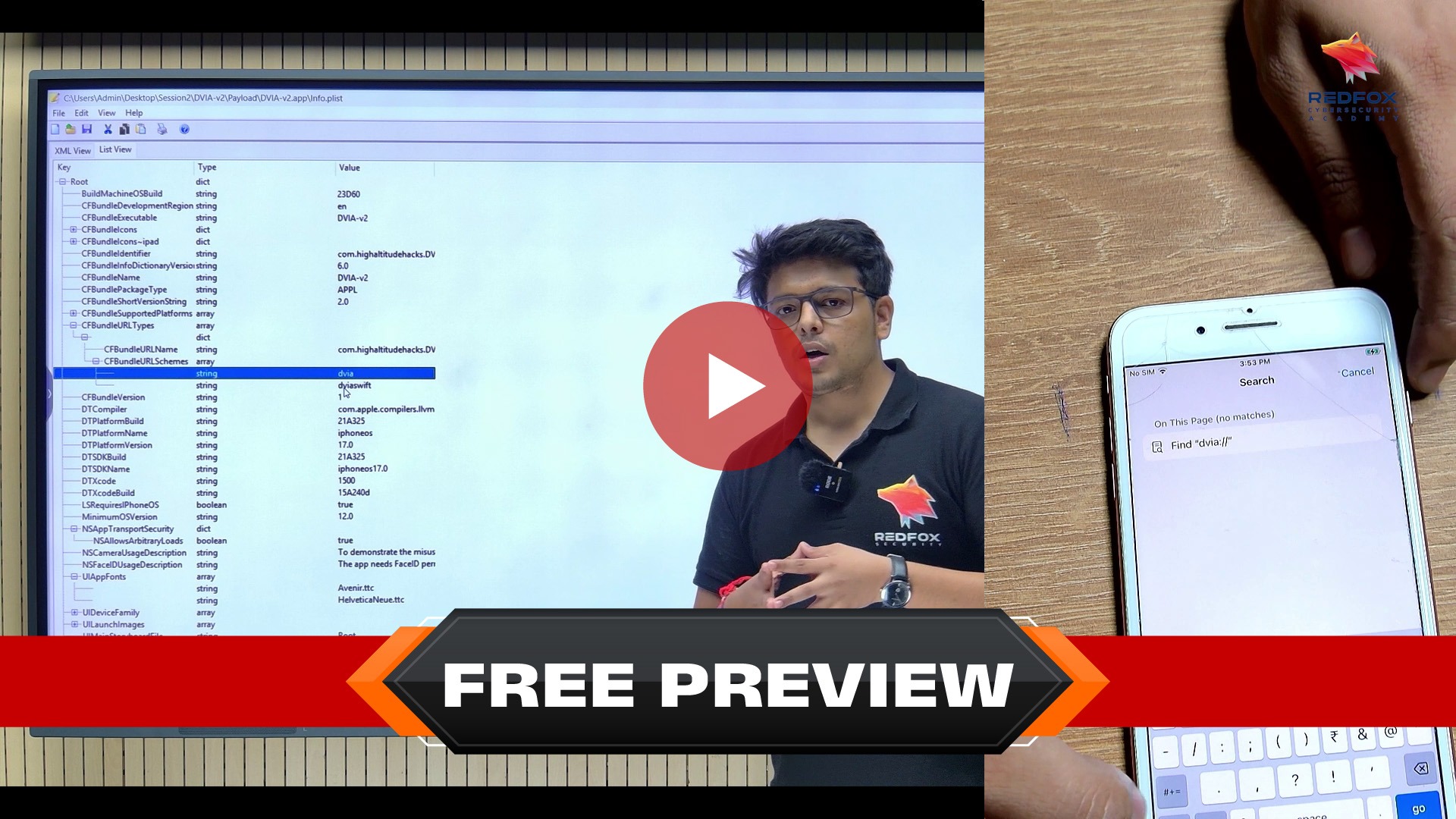
Introduction to Static Analysis and Reverse Engineering
Install Otool on IOS Device
Application Extraction
iOS App Architecture
Static Analysis (Automate)
Decompile the App
Static Analysis (Manual)
Reverse Engineering
SAST Recap
Module 4: Dynamic Application Security Testing (DAST)
Agenda
Introduction to Dynamic analysis
Configure Burp Suite with IOS Device
Runtime Manipulation
Summary And Key Takeaways
Module 5: iOS Application Attack Surface
Agenda
iOS Penetration Testing Checklist
Attack Surface
Insecure Local Data Storage
Side Channel Data Leakage
Inter-Process Communication (IPC) Issues
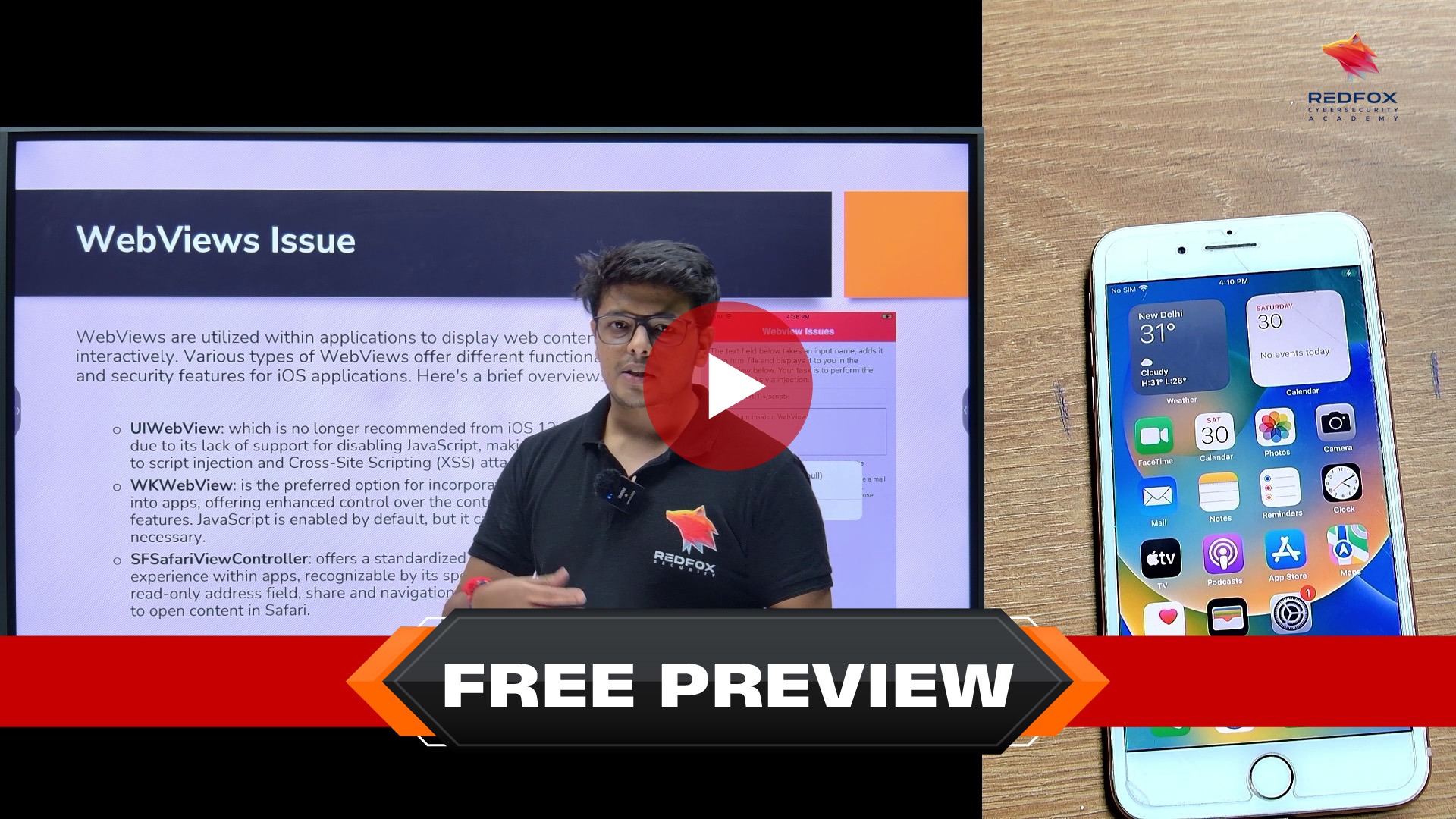
WebViews Issues
Sensitive Information in Memory
Session Recap – Conceptual Walkthrough
Report Writing
Summary & Key Takeaways
Module 6: Course Resources
Frida-IOS-Dump
Mobile-Reporting-Template
IOS-Pentesting-Checklist
IOS-Pentesting-Course-PPT
Module 7: Certification and Exam
Certification and Exam
iOS Pentesting Course Instructor

Atharva Nanche
Security Consultant
Atharva Nanche is a cybersecurity enthusiast with expertise in web, mobile, API, thick client, and network security. He focuses on finding and fixing vulnerabilities to secure digital ecosystems.
Certified iOS Application Penetration Tester (CIAPT)
Earning the CiAPT certification demonstrates your expertise in iOS application security, including identifying and exploiting real-world iOS vulnerabilities, securing iOS apps, and performing live exploitation techniques. The certification enhances your career prospects, making you stand out for roles such as iOS penetration tester, security analyst, or mobile security researcher.

Who Should Take this Course?
- Penetration testers and security professionals who want to specialize in mobile application security.
- Developers looking to secure their iOS apps and understand how attackers target mobile platforms.
- IT professionals and enthusiasts interested in gaining hands-on experience in iOS pentesting.
- Students aiming to build a career in cybersecurity with a focus on mobile security.
iOS pentesting is rare, highly paid, and in demand...
this course puts you in that category.
Ready to Master the Art of Pentesting?
Affordable Price
Unlock your potential with affordable upskilling! Our unbeatable course prices are your chance to level up without breaking the bank.
Lifetime Access
Acquire lifetime access to our resources when you buy our courses. Gain knowledge today and unlock a lifetime of learning.
Certificate of Completion
Upon completing our course, you'll receive a certificate of completion to showcase your new skills. Add it to your resume or LinkedIn profile.
Hands-On Experience
Get hands-on experience with real-world scenarios and challenges, giving you practical skills that you can apply immediately in your career.
Expert Instructors
Learn from industry experts with years of experience in pentesting, who are passionate about sharing their knowledge and helping you succeed.
Flexible Learning
Whether you're a beginner or an experienced professional, our courses are designed to meet you where you are and help you reach your goals.
Get in Touch
Have a question, need assistance, or want to collaborate? We’re here to help!
Whether you're looking for cutting-edge cybersecurity solutions or expert training or want to learn more about our services, contact us today.
By clicking on Continue, I accept the Terms & Conditions,
Privacy Policy & Refund Policy