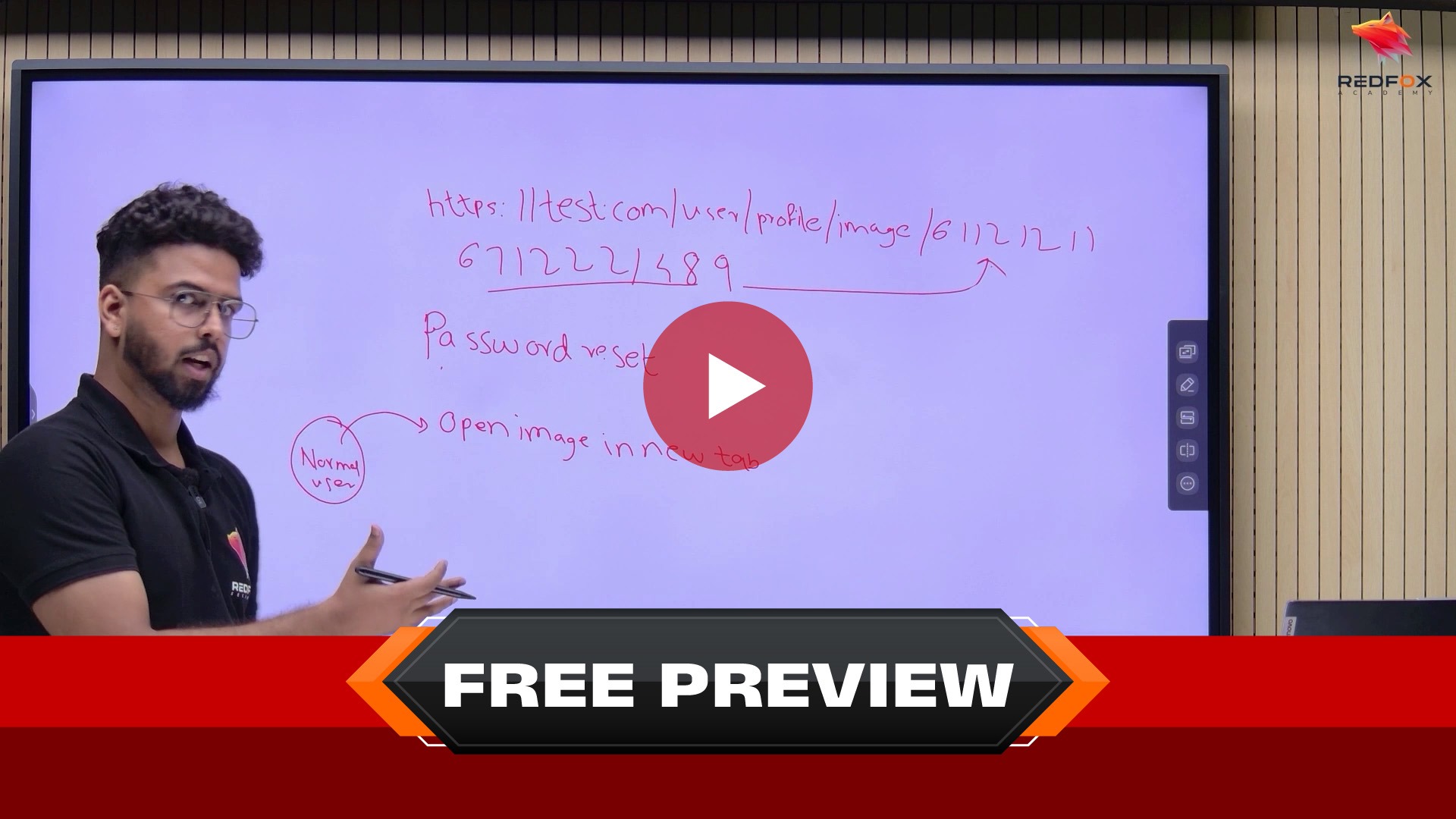
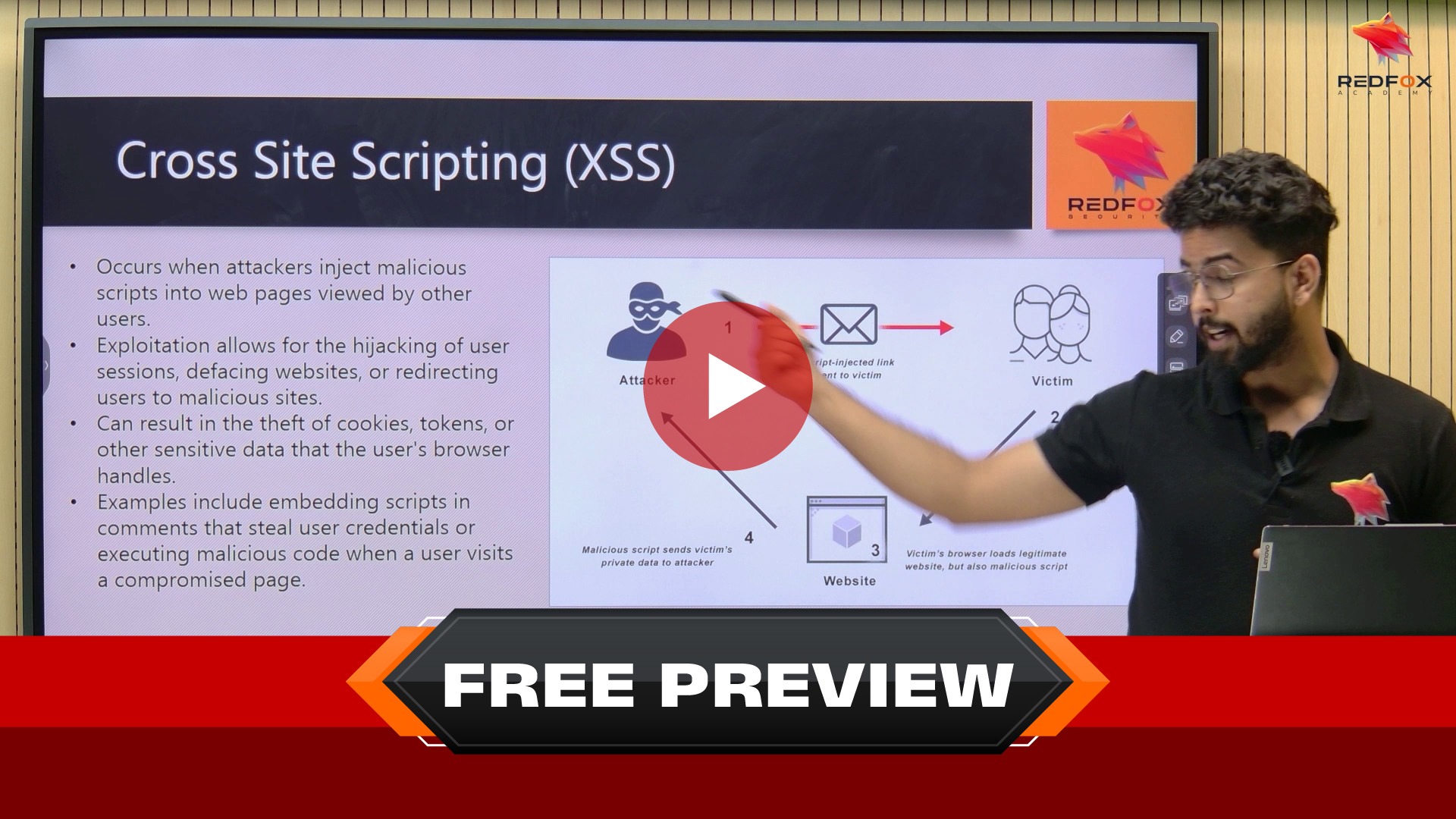
Testimonials
DR
The practical depth of the Web Hacking Advanced Course at Redfox Cybersecurity Academy impressed me the most. The labs simulate real-world attack scenarios and force you to think critically. Tarak Sakhardande delivers advanced topics in a structured and easy-to-follow manner. This course has significantly strengthened my technical confidence and analytical skills.
Read more
AJ
January 7
The Web Hacking Advanced Course at Redfox Cybersecurity Academy truly elevated my skills. The program is heavily focused on practical learning, with detailed labs that push you to apply every concept immediately. Tarak Sakhardande explains advanced techniques with real-world clarity, which made complex topics much easier to grasp. I now approach web security assessments with far more structure and confidence.
Read more
RZ
October 27, 2025
What sets Redfox Cybersecurity Academy apart is the strong emphasis on hands-on practice. Most of the learning happens inside labs, which helped me move beyond theory. Tarak Sakhardande ensures every advanced vulnerability is demonstrated practically before moving ahead. This course significantly sharpened my technical thinking and attack methodology.
Read more
Sophia Miller
December 1, 2025
The Web Hacking Advanced Course at Redfox Cybersecurity Academy goes deep into advanced vulnerabilities like Server-Side Request Forgery, advanced SQL Injection techniques, authentication bypass, and complex access control issues. Learning these through hands-on labs made a huge difference. Tarak Sakhardande connects each topic to real-world exploitation scenarios, which made the content extremely practical and impactful.
Read more
Lucas Thompson
October 28, 2025
I appreciated how Redfox Cybersecurity Academy focuses on practical learning rather than just presentations. The majority of the course involves hands-on lab work, which helped me internalize advanced exploitation techniques. Tarak Sakhardande explains not just how attacks work, but why they work. That clarity made a huge difference in my understanding.
Read more
KP
October 16, 2025
The Web Hacking Advanced Course at Redfox Cybersecurity Academy pushed me to think at a much deeper level. The course covers topics like advanced XSS exploitation, file upload vulnerabilities, business logic flaws, and chaining multiple vulnerabilities together. Practicing these in structured labs helped me understand real attack flows. Tarak Sakhardande brings strong practical insights into every session.
Read more